Why Port Scanning is considered "First line of cyber Attack"?
Meaning of the term
Since all our computer services rely on various number of ports to function. As like when I want to send an email to my friend, my computer's server will open a port through which a new mail will be sent through a connection to the email server.
Some ports on someone’s computer are open continually, making them a target for any potential hacker who is searching for target. This can lead to one's sensitive and personal information falling into the hands of those who intend on using it for criminal activity. Unfortunately, criminals and computer hackers are always looking for new victims to exploit, and port scanning is one of the ways through which this can be accomplished.Port scanning is one of the methods of attacking any system, it basically means the technique to identify all the open ports and the services which are available on any network host. There are many ports on a system but the only goal for this attack is to find an active open port and exploit a known vulnerability. (It can be used to send client requests to the target hosts, and then analyse which ports appear to be opened, or those that respond to the request.)
For the very long time people are using scanning, as a method for discovering exploitable communication channels. Like when a thief targets a house to steal something from, basically the first thing he does is to check if there is any open window or door through which he can get access to the target house. A Port scan is like the same, but only the windows and doors are replaced with ports of the target host. The attacker (in this case a Hacker) then has to decide whether it is easy to go inside from this window (or door) or not, it is up to him.
Just checking to see if a possible connection could be made is not a crime as anyone (as a valid user) can see for connection, but doing it in repetition can also act in a DoS attack.
Most Hackers basically uses port scanning because it is a very easy way in which they can discover services they can break into in a very short time. Still in some cases, some hackers can even open the ports by themselves in order to gain access to the target host. Hackers use port scanning tools to conduct the tests for open ports on the target hosts that are connected to the web.
There are 65536 distinct and usable port numbers. Most of the popular services use a limited range of numbers.
The port numbers are divided into three ranges: the Well Known Ports, the Registered Ports, and the Dynamic and/or Private Ports.
Ø The Well known Ports are those from 0 through 1023.
Ø The Registered Ports are those from 1024 through 49151.
Ø The Dynamic and/or Private Ports are those from 49152 through 65535.
There is also a method for mass scanning known as Portsweep.
Portsweep differs from portscan, in portsweep multiple hosts are scanned for a specific listening port. For example, if the attacker would like to find out all the webservers which is running in the target network, Portsweep is used against port 80 and 443 towards all the hosts in the network.
Some of the most commonly used ports and applications on the "Well known ports" category (From port 0 to 1023) are
- 20 FTP data (File Transfer Protocol).
- 21 FTP (File Transfer Protocol).
- 22 SSH (Secure Shell).
- 23 Telnet.
- 25 SMTP (Send Mail Transfer Protocol).
- 53 DNS (Domain Name Service).
- 68 DHCP (Dynamic Host Control Protocol).
- 80 HTTP (HyperText Transfer Protocol).
- 110 POP3 (Post Office Protocol, version 3).
- 115 SFTP (Secure File Transfer Protocol).
- 143 IMAP (Internet Message Access Protocol).
- 161 SNMP (Simple Network Management Protocol).
- 194 IRC (Internet Relay Chat).
- 220 IMAP3 (Internet Message Access Protocol 3).
- 443 SSL (Secure Socket Layer).
When the network scan has been completed and a list of available hosts has been compiled, a port scan can be used to identify the in use on specific ports by the available hosts. Port scanning will typically classify ports into one of three categories:
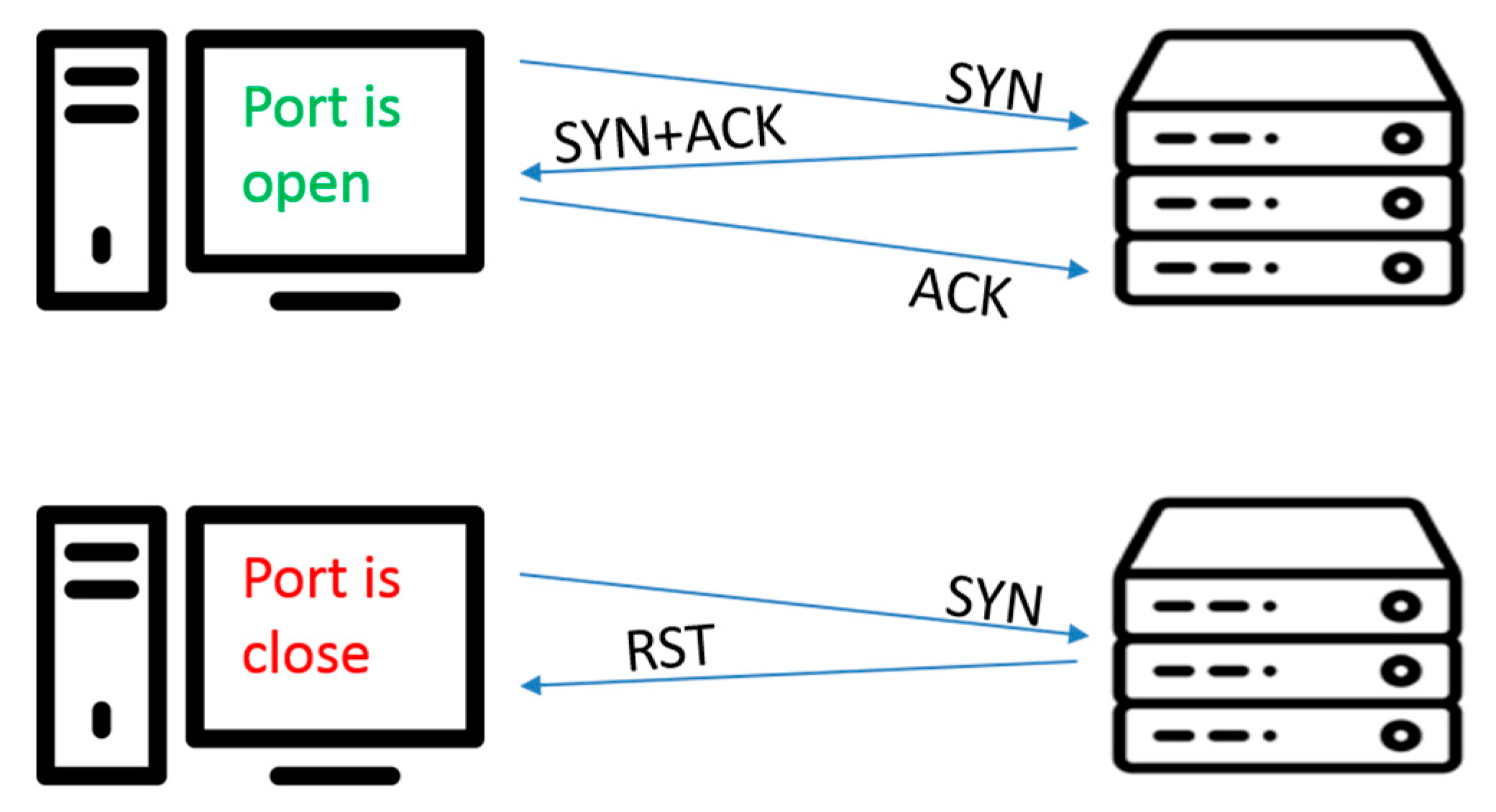
Open: The target host responds with a packet indicating it is listening on that port. It also indicates that the service that was used for the scan (typically TCP or UDP) is in use as well.
Closed: The target host received the request packet but responds back with a reply indicating that there is no service listening on that port.
Filtered: A port scan will categorize a port as filtered when a request packet is sent but no reply is received. This typically indicates that the request packet has been filtered out and dropped by a firewall.
--------------------------------------------------------------------------------------------------------------
TYPES OF SCANS
There are several types of scans that can be used -
![]() TCP connect scanning:
TCP connect scanning:
o TCP connect scanning is the most basic form of TCP scanning. The connect() system call provided by the operating system is used to open a connection to any port on the target machine. If the port is listening, connect() scanning will succeed, otherwise the port will not be reachable.
Advantages:
- The attacker does not require any special privileges to scan.
- Scanning can be performed much more quickly as the speed of the scan is higher.
Disadvantages:
- Easily detectable by IDS and IPS systems. And many operating systems can detect these type of connection attempts.
![]() TCP SYN scanning:
TCP SYN scanning:
o TCP SYN scanning is also known as "half-open" scanning, as the originator / attacker does not open a full TCP connection. The attacker sends a SYN packet and wait for a response. A SYN|ACK response from the target indicates the port is listening and as soon as a SYN|ACK is received the originator or the attacker sends a RST response.
Advantages:
- Most of the target hosts does not log this attempt.
Disadvantages:
- There are no disadvantages of this type of scanning.
![]() TCP FIN scanning:
TCP FIN scanning:
o Most of the firewalls and IPS devices moniter, detect and filter SYN based scanning. But many firewalls and IPS devices allow FIN packets. When the FIN packets are sent by the attacker to the target, the closed ports reply with the RST packet response, whereas open ports ignore the FIN packets sent by the attacker. While this method works in in the unix based systems, Microsoft windows based operating systems send RST packet responses to the attacker in the both the conditions whether the port is closed or open. Hence it could be also used to distinguish between windows and Unix hosts.
Advantages:
- Can be used to evade many firewall and IPS systems.
Disadvantages:
- There are no disadvantages of this type of scanning.
![]() Fragmentation scanning:
Fragmentation scanning:
o Fragmentation scanning is performed for evading the firewalls and other packet filtering devices by sending the TCP headers in small tiny fragments, which may confuse the firewalls and other devices when processing packets. While many firewalls can queue the packets for assembling, this type of scanning can consume the processing power of the victim host or the devices which are in the front of the victim IP addresses.
Advantages:
- Can be used to evade many firewall and IPS systems.
Disadvantages:
- Scanning can have a negative impact on the target devices and other devices which is on the path.
How can an attacker use a port scan to perform an attack:
There are multiple ways of using a port scan as –
1. Ping Scan
The simplest port scans are ping scans. A ping is an Internet Control Message Protocol (ICMP) echo request – we are looking for any ICMP replies, which indicates that the target is alive. A ping scan is an automated blast of many ICMP echo requests to different targets to see who responds.
Administrators usually disable ping either on the firewall or on the router. It’s quick and easy to turn off this functionality and make it impossible to scout the network this way. However, ping is a good troubleshooting tool, and turning it off makes tracking down network problems a little more difficult.
2. TCP Half-Open port scan
One of the more common and popular port scanning techniques is the TCP Half-Open port scan, sometimes referred to as SYN scan. It’s a fast and sneaky scan that tries to find potential open ports on the target computer. This scan is fast because it never completes the full TCP 3 way-handshake. The scanner sends a SYN message and just notes the SYN-ACK responses. The scanner doesn’t complete the connection by sending the final ACK: it leaves the target hanging.
Any SYN-ACK responses are possible connections: an RST(reset) response means the port is closed, but there is a live computer here. No responses indicate SYN is filtered on the network. Any SYN-ACK replies are a quick way cybercriminals can find the next potential target.
3. TCP connect
This port scanning technique is basically the same as the TCP Half-Open scan, but instead of leaving the target hanging, the port scanner completes the TCP connection.
It’s not as popular a technique as the TCP Half-Open. First, I have to send one more packet per scan, which increases the amount of noise I are making on the network. Second, since I complete the connection with the target, I might trip an alarm that the Half-Open scan wouldn’t.
4. UDP scan
UDP is the other half of our “hallway” and some standard services – DNS, SNMP, DHCP for example – use UDP ports instead of TCP ports. When I run a UDP port scan, I send either an empty packet or a packet that has a different payload per port, depending on my use case.
5. Stealth Scan
When we send a port scan with a packet and the FIN flag, we are sending the packet and not expecting a response. If I do get an RST we can assume that the port is closed. If we get nothing back that indicates the port is open. Firewalls are looking for SYN packets, so FIN packets slip through undetected.
6. Vanilla
The most basic scan; an attempt to connect to all 65,536 ports one at a time. A vanilla scan is a full connect scan, meaning it sends a SYN flag (request to connect) and upon receiving a SYN-ACK (acknowledgement of connection) response, sends back an ACK flag. This SYN, SYN-ACK, ACK exchange comprises a TCP handshake. Full connect scans are accurate, but very easily detected because full connections are always logged by firewalls.
7. FTP Bounce Scan
Allows for the sender’s location to be disguised by bouncing the packet through an FTP server. This is also designed for the sender to go undetected.
8. Sweep scan
Pings the same port across a number of computers to identify which computers on the network are active. This does not reveal information about the port’s state, instead it tells the sender which systems on a network are active. Thus, it can be used as a preliminary scan.
----------------------------------------------------------------------------------------------------------------
Impact on Victim’s system:
At some point of time there are multiple open ports on one's computer, there is potential for the loss of data, the occurrence of a virus, and at times, even complete system compromise. It is essential for one to protect his or her virtual files, as new security risks concerning personal computers are discovered every day. Computer protection should be the number one priority for those who use personal computers. Port scanning is considered a serious threat to one's PC, as it can occur without producing any outward signs to the owner that anything dangerous is taking place.
Protection from Port Scanning:
![]() Protection
from port scanning is often achieved through the use of a firewall. A firewall
monitors incoming and outgoing connections through one's personal computer.
Protection
from port scanning is often achieved through the use of a firewall. A firewall
monitors incoming and outgoing connections through one's personal computer.
o One technique used by firewall technology is the opening of all the ports at one time. This action stops port scans from returning any ports. This has worked in many situations in the past, however, most experts agree it is best to have all open ports investigated individually.
o Another approach is to filter all port scans going to one's computer. An individual can also choose to port scan his or her own system, which enables one to see the personal computer through the eyes of a hacker.
![]() Firewalls
are the best protection one can invest in with regard to port scanning.
Firewalls deny outside access to an individual's personal computer. With this
type of protection, a personal computer is essentially hidden from unwelcome
visitors and is also protected from a variety of other hacking techniques. With
firewall software, an individual is assured that his or her sensitive and
personal information remains protected.
Firewalls
are the best protection one can invest in with regard to port scanning.
Firewalls deny outside access to an individual's personal computer. With this
type of protection, a personal computer is essentially hidden from unwelcome
visitors and is also protected from a variety of other hacking techniques. With
firewall software, an individual is assured that his or her sensitive and
personal information remains protected.
~ Thank you for reading this post ~
🙏

Comments
Post a Comment